Why Phishing Matters To Your Business
A discussion on the basics of phishing attacks and how they can impact your growing business.
PHISHINGCYBERSECURITYBUSINESS
Trevor Winge
9/7/20235 min read


Phishing Attack Overview
Phishing attacks are commonly conducted through deceptive means, aiming to trick individuals into divulging sensitive information such as passwords, credit card details, or personal data. These attacks typically start with an email or message that appears to be from a reputable source, such as a bank or a popular online service. The message often urges the recipient to click on a link or provide their login credentials under the pretense of a security verification or urgent matter. Once the victim interacts with these malicious links or provides their information, the attackers gain unauthorized access to their accounts, enabling them to steal personal or financial data. Phishing attacks can also be carried out through phone calls, text messages, or fake websites. It is crucial to remain vigilant and cautious while online in order to avoid falling victim to these fraudulent schemes.
Impacts to Small Businesses
Phishing attacks have a severe impact on small businesses, causing significant financial and reputational damage. These malicious attempts aim to deceive employees into sharing sensitive information, such as login credentials or financial data, by posing as trusted sources. Once the attackers gain access to this information, they can exploit it for various purposes, including unauthorized transactions or identity theft. Small businesses often lack robust cybersecurity knowledge and can be easy targets for phishing scams. The consequences have the potential to be devastating, with substantial financial losses, compromised customer data, and shattered trust. Moreover, the time and resources required to recover from such attacks can cripple the operations of a small business, impeding growth and hindering their ability to compete in the market. Therefore, it is vital for small businesses to prioritize cybersecurity awareness and education to mitigate the risks posed by phishing attacks.
Real Life Phishing Attack
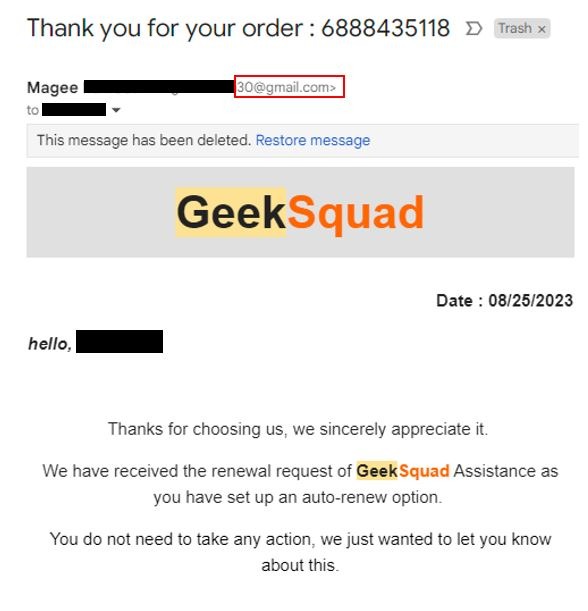
I was recently the subject of a phishing attack. I received an e-mail stating that I completed an order with BestBuy's Geek Squad.
NOTE: As a disclaimer I have modified the original phishing e-mail to block out my personal information along with the sender's e-mail address on the chance that it belongs to a victim of identity theft.
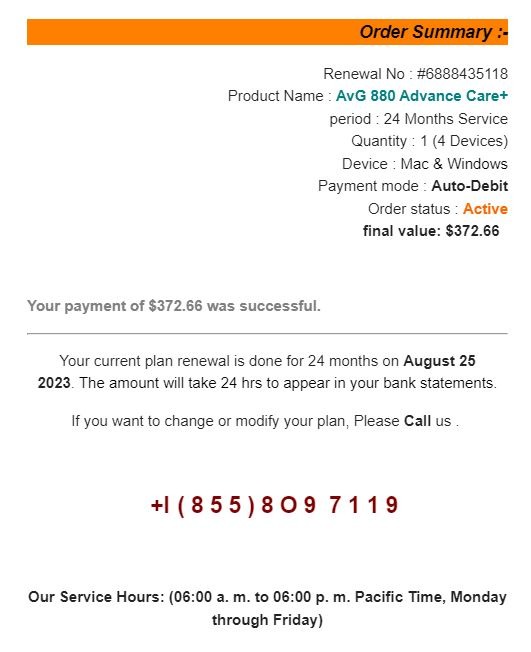
Let's breakdown this phishing attack. Upon first glance this looks like it could be a legitimate order. It has all the fundamental components: order number, date, company logo, order summary, quality e-mail structure. The scenario that is created is that I have been charged $372.66 and this charge is going to reoccur every 24 months. This creates a sense of urgency as I do not wish to be charged anything and I certainly do not wish to be set-up with an auto-renew option. Luckily they provide a customer support number that I can call and get this whole issue resolved.
Here are red flags:
I have never ordered Geek Squad services
The sender's e-mail is a Gmail account
The message creates a sense of urgency
There is specific text formatting to shape the receiver's next reaction
Grammar inconsistency with capitalization
Oddly formatted telephone number
1. Unexpected e-emails are typical of a phishing attacks. A standard attack is designed to be sent to many recipients. Even if the attacker gets a one percent response, that would be considered a success. This is why you need to be extra cautious when dealing with unsolicited or uncommon e-mails.
2. It is easy to create a free e-mail account with services like Yahoo or Google. When getting what looks like a professional business e-mail, I would expect to see a business domain at the end of the e-mail. In this example we can see they are using a Gmail account to send the attack. Many small business do use Gmail and Yahoo for their business needs but it very abnormal for larger businesses such as BestBuy.
3. Almost every phishing attack will try and create a sense of urgency. Typically they will create a situation where you can solve a problem by providing some sensitive information or money. I didn't call the number in this attack but they would have likely asked me to verify my banking or credit card information so they could "refund" me the money.
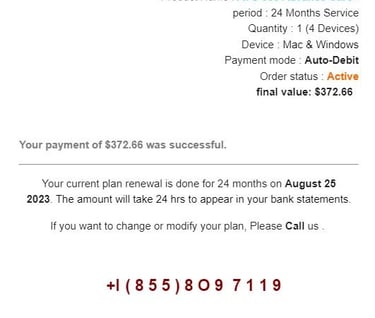
4. In this attack, we can see that they are bolding text to drive my actions. So "Geek" is bolded first and this makes the bolding appear to be a normal thing. The next bolding is "Auto-Debit". This is intended to drive the fear that I am automatically paying for something I don't want. Then the price is bolded, which is a concerning value for most folks and could easily cause financial issues. Next is the date of the order which, corresponds with the date the e-mail was sent. Finally, the attacker bolds the word "Call". This is the action they are wanting me to take.
5. Looking for grammar mistakes used to be a good sign of a non-native speaker. Many large scale phishing attacks originate outside of the United States and poor grammar was a quick way to get a feeling that something wasn't right. The development of "spell-check" and chat bots have significantly decreased the grammar errors in many attacks. The message in this attack is well constructed. What stood out to me was the capitalization in the Order Summary. A professional template would capitalize "period" and "final". Additionally, the odd capitalization of the word "Call" near the end of the message was out of place.
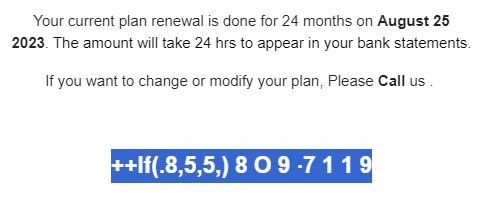
6. The final item we will cover is the actual phone number they provided. Upon initial glance it looks like most telephone numbers. The "O" is the first thing that caught my eye. The difference between "O" and "0" are typically very subtle but in just about every font there is a slight difference with the zero being a bit more oval. Then we see that there are three "1"s in the number but one of them is a bit different than the others. This is enough to raise suspicions but we can take it a step further. Just by highlighting the text we can see that the phone number is formatted to bypass automated scam number phone scanners.

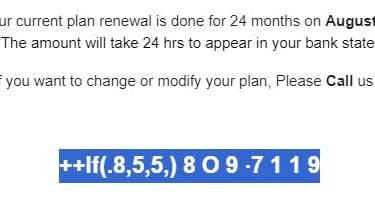
Summary
It doesn't matter if you have a personal e-mail or business e-mail, you will get phishing attacks. A heathy dose of suspicion can save a business from a costly cyber attack. This example was likely a money scheme designed to have me reveal some financial information. Other phishing attacks can have the purpose of harvesting credentials. If those credentials give them access to business accounts, then the impact can be extremely severe. You must be vigilant with all forms of communication.


